If you own any cryptocurrency, you know you need a safe place to keep it because cryptocurrency is one of the most irreparable assets that are lost or stolen. This means explaining your crypto wallet to you in a simple and clear way.
A crypto wallet is different from the one you keep a typical wallet and is kept in cash and cards, usually a software program on your computer or an application on your mobile device. Crypto wallets store crypto assets, but using them correctly means keeping them and your coins safe.
In this guide, you will learn not only what a normal wallet is, but how crypto wallets work, which type is best for certain situations and why this is all important. Finally, you will have a solid foundation that will go a long way in ensuring the security of your crypto assets, whether you are trading or scammers.
What is a crypto wallet?
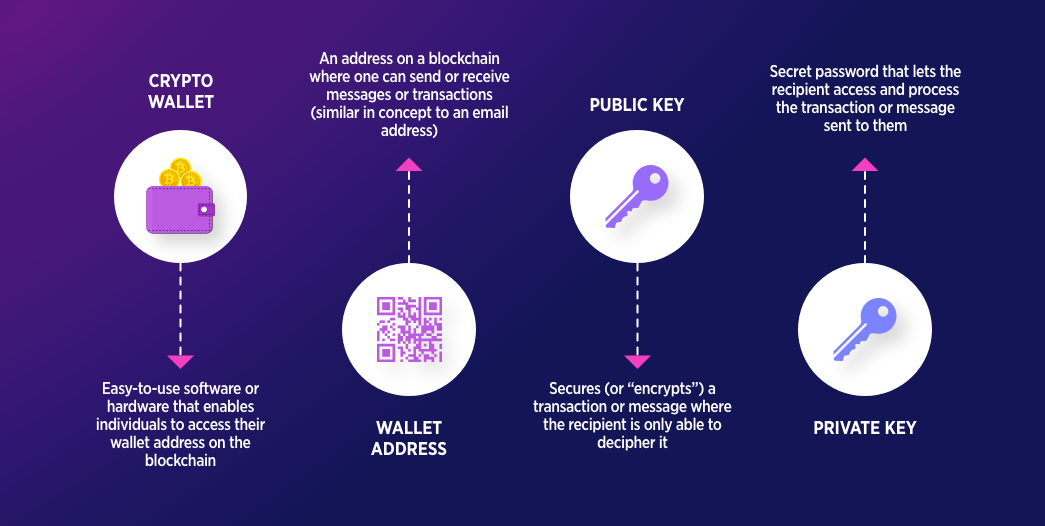
Crypto Wallet is a digital interface that allows crypto owners to manage the public and private keys needed to interact with the blockchain. Unlike traditional wallets that store physical assets, Software wallet Store the private key.
The private key is long, complex alphanumeric characters that prove ownership of a particular chain asset. When the Wallet software first creates a new address, it generates a seed phrase that can be used to restore assets if you lose access to the actual physical device of the key storage.
A wallet connected to the internet also displays a public key or public address associated with a specific wallet. These addresses are publicly visible destinations on the blockchain that sends cryptocurrencies.
Why is crypto wallet important?
The biggest thing that makes crypto wallets important is that they can directly and explicitly control the digital assets stored in them without having to rely on banks, brokers or other third parties.
When you have your own private key, you eliminate all opponent risks. This means your assets are completely out of exchange hackers, account freezes and similar unforeseen liquidity clearance events. Wallets also provide the basis for permissionless DAPP access, so you can borrow, borrow, trade encryption and even mint NFT in seconds by connecting your wallet to the appropriate platform.
Last but not least, wallets are the basis of encryption security measures. Cold wallets store private keys in cold storage, while “hot wallets” or online wallets secure private and public keys with two-factor authentication and biometric security measures. Thanks to a crypto wallet is Unused wallet With your first line of defense
How does a crypto wallet work?
Crypto wallet manages two key information at its core: a public key (your wallet address) and a private key (your digital signature). When someone sends you a cryptocurrency, the transaction will be recorded on the blockchain under your public address.
To move these funds elsewhere, you must prove ownership by signing the transaction with your private key. Wallet software handles this signature process behind the scenes, broadcasting signed transactions to network verification. Because the private key never leaves your device, you can only authorize your assets to move.

How to execute transactions in a crypto wallet?
- First, you need to generate a transaction by entering the recipient’s address and sending the encrypted amount of the wallet interface.
- Next, your wallet will use your private key to create signatures to sign the transaction to prove that you own the funds and are authorized to spend them.
- Now that the cryptocurrency transaction is ready, it has been broadcast to the blockchain network where it is included in the network.
- Notes then verify the signature of the public key and state that it is valid and that the wallet balance is sufficient, the transaction has been verified and accepted on the blockchain.
- Transactions become part of the blockchain network ledger and are then used to confirm future transactions. Most transactions are considered “complete” until a specific number of confirmations is obtained in the network.
Different types of crypto wallets
The biggest difference between a crypto wallet option is between a hosted wallet and a non-custodial wallet. Let’s take a look at the differences between these types of wallets and then look at some real-world examples.
Hosted wallet
Hosted wallets are various wallets managed through exchanges or fintech services such as Robinhood and Cash App. Although they have a great user-friendly interface and feel like traditional online wallets, you enjoy the security of your provider. If you lose access, your wallet provider will usually restore it.
Source: Robinhood.com
Unused wallet
Non-habitual wallets can keep your private keys secure by fully controlling them. You generate seed phrases and are responsible for keeping them offline. These wallets are real self-customers and if you lose your private key, you will not be able to execute any blockchain transactions.
Hosting vs. Non-habitual crypto wallets: The key difference
| feature | Hosted wallet | Non-customer wallet |
| Key control | Third party (exchange, service) retain keys | User control private key |
| recover | Providers can reset access | Only seed phrase recovery access |
| Ease of use | Usually simple account-based login | Need key management and backup |
| risk | Adversary risk (hacker, freeze) | Personal liability; loss of key = loss of funds |
| Ideal | Short-term transactions for beginners who trust providers | Long-term holding, Defi user, owned by itself |
Hot wallet
Hot wallets are software wallets connected to the internet.
- Desktop wallet: Desktop PCs and laptops often have access to fully functional interfaces, local key storage, and even run verification nodes. Perfect for users who want full device control.
- Mobile wallet: Mobile wallets are common for Android and iOS, and these software wallets store private and public keys for quick access as well as quick access and carry-on asset management in simple digital tools. They usually have biometric or pin protection.
- Online wallet: A web wallet is a browser-based wallet or exchange account wallet that can be accessed from almost any device. These are the peaks of convenience, but arguably the least secure choices of all conveniences.
Cold wallet
Cold wallets store your private key offline, which reduces the potential attack surface to nearly zero.
- Paper wallet: Paper wallets were once a convenient way to give people Bitcoin wallets in the early 2010s to help them gain popularity. They are a printed sheet of paper with a public key and QR code that unlocks the wallet.
- Hardware wallet: Hardware wallets are specialized devices like the Ledger Nano that all generate and securely store the keys in a tamper-proof chip. Transactions are signed from within the device, reducing the possibility of private key vulnerabilities.
How is hot wallet different from cold wallets?
| feature | Hot wallet | Cold wallet |
| Internet connection | Online or frequently connected | Stay offline (open space) |
| convenient | Instant access to daily use | Slower, best for long-term storage |
| Security risks | Vulnerable to malware, phishing | Refrain from online hackers; physical theft risk |
| Typical form | Desktop, mobile, network extension | Paper wallet, hardware equipment |
| Ideal | Small and medium balance, active transaction | Large shares, “Hold” investors |
The best crypto wallet comparison
| wallet | Wallet Type | custody | Cold/cold wallet | Supported chain stores* | Key Features |
| LEDGER NANO X | hardware | Non-customer | Cold | 1,000+ (BTC, ETH, SOL, etc.) | Bluetooth, security elements, stillness, defi |
| Trezor model T. | hardware | Non-customer | Cold | 1,000+ | Touch screen, open firmware, Shamir backup |
| metamask | software | Non-customer | Hot | Ethereum, EVM chain | Browser/mobile device, Defi switch, hardware – Wallet pairing |
| Coinbase wallet | software | Non-customer | Hot | Multi-chain (ETH, SOL, etc.) | Built-in DEX, NFT gallery, ENS support |
| Trust the wallet | software | Non-customer | Hot | More than 70 blockchains | Move, stack, in-app exchange, DAPP browser |
How to protect encrypted wallets?
- Take your private key offline, a safe place. If you don’t control the key, you can’t control the coins.
- Always use 2FA or MFA on your hot wallet and exchange accounts.
- Never store seed phrases online. Leave them within the range of fire and floods.
- Always use hardware wallets for a larger portfolio.
- Place multiple redundant backups of seed phrases in different locations.
Best Practices for Crypto Wallet Management
- Segmented funds: Keep daily spending (hot) wallets and keep a cold wallet for long-term offline storage.
- Testing small transfers: Please send a small test transaction to confirm the address before moving large sums.
- Stay informed: Follow wallet provider announcements for security advice or feature updates.
- Tag address: Use a wallet tag or contact list to avoid sending funds to the wrong account.
- Revoke unused DAPP permissions: Regular review and revoke token approvals to limit smart contract risks.
- Monitoring activities: Use Explorer or Portfolio Tracker to view any unauthorized transactions.
- Practice a safe browsing: Phishing attacks are very common; install anti-phishing browser extensions to avoid clicking unknown links.
- Education trustworthy contact person: If you share assets with your family or partners, make sure they are aware of the recovery procedures.
in conclusion
Crypto wallets form the foundation of the self-customer crypto world and provide you with real ownership of assets. They let you manage your cryptocurrency holdings as you see fit. Regardless of which hardware or software wallet you decide to use, make sure you follow security best practices and keep all devices updated and patched to help you protect your holdings for the long term.
FAQ
Which crypto wallet is the best?
There is no answer for a size. If you are looking for peak security, a hardware wallet like Ledger or Trezor will lead the package. For daily convenience, it is difficult to beat the meta bunker or twenty coinbase wallets, which all offer intuitive interfaces and multi-chain support.
What is the best secure wallet for cryptocurrencies?
Hardware wallets provide the highest level of security as private keys remain offline. The Ledger Nano X and Trezor T Model T are the industry standards for refrigeration.
Can you convert your crypto wallet to cash? How do you cash out your encrypted wallet?
Yes, you can easily convert your crypto wallet to cash. To cash out, you need to transfer the cryptocurrency from your personal wallet to a reputable exchange, sell it in Fiat currency, and then withdraw your bank account. Some wallets also integrate the post-needed/outward service of direct cash bins.
How to use a crypto wallet?
Download or set up your wallet, securely store your seed phrases, fund your wallet by receiving cryptocurrency to your public address, and sign transactions with your private key to send or interact with the DAPP.
Is crypto wallet safe?
Wallets are as secure as security practices. Non-customer wallets maintain control, but you must protect the keys. Hardware wallets and strong operational security greatly reduces risks, while poor key management can lead to losses.

